Top Guide To The Best IoT Remote SSH Connection: Secure & Efficient Solutions
Managing IoT devices remotely has become a cornerstone of modern technology ecosystems, with SSH (Secure Shell) connections playing a pivotal role in ensuring secure and reliable access. The best IoT remote SSH connection allows users to interact with devices from anywhere in the world, ensuring seamless control, configuration, and troubleshooting. As IoT deployments grow in complexity and scale, the demand for robust remote access solutions continues to rise. In this article, we will explore the importance of SSH in IoT environments, uncover the key features that define the best IoT remote SSH connection, and provide actionable insights to help you choose the right solution for your needs. Whether you're managing smart home devices, industrial sensors, or enterprise-grade IoT networks, understanding how to establish secure and efficient remote connections is essential for success.
IoT devices often operate in distributed environments, making remote management a necessity rather than a luxury. SSH provides a secure communication channel that encrypts data in transit, safeguarding sensitive information from unauthorized access. By leveraging the best IoT remote SSH connection tools, administrators can execute commands, transfer files, and monitor device performance without physical proximity. This capability not only enhances operational efficiency but also reduces downtime and maintenance costs. With the right SSH solution, users can ensure that their IoT networks remain resilient, scalable, and protected against potential cyber threats.
However, not all SSH tools are created equal, and selecting the best IoT remote SSH connection requires careful consideration of several factors. These include ease of use, compatibility with your IoT devices, scalability to accommodate future growth, and advanced security features like multi-factor authentication and intrusion detection. Additionally, the best solutions offer intuitive interfaces, cross-platform support, and seamless integration with existing infrastructure. By the end of this article, you'll have a comprehensive understanding of the criteria for selecting the best IoT remote SSH connection and the tools that stand out in the market today.
Read also:Henry Cavill Upcoming Movies A Comprehensive Guide To His Future Projects
Table of Contents
- What Makes an IoT Remote SSH Connection the Best?
- How Can You Ensure Security in IoT Remote SSH Connections?
- Why Is Cross-Platform Compatibility Crucial for IoT SSH Tools?
- What Are the Top Tools for IoT Remote SSH Connections?
- How to Optimize SSH Performance for IoT Devices?
- What Are the Common Challenges in IoT Remote SSH Connections?
- How to Troubleshoot Issues in IoT SSH Connections?
- Frequently Asked Questions About IoT Remote SSH
What Makes an IoT Remote SSH Connection the Best?
When evaluating the best IoT remote SSH connection, several key factors come into play. First and foremost is security. SSH protocols are designed to encrypt data in transit, but the best tools go a step further by incorporating advanced features like key-based authentication, multi-factor authentication (MFA), and real-time intrusion detection systems. These features ensure that even if credentials are compromised, unauthorized access remains nearly impossible. Additionally, the best IoT remote SSH connection tools offer granular access controls, allowing administrators to define user roles and permissions based on specific tasks or device groups.
Another critical aspect is ease of use. The best IoT remote SSH connection tools provide intuitive interfaces that cater to both novice users and seasoned IT professionals. Features like drag-and-drop file transfers, command history, and customizable shortcuts can significantly enhance productivity. Furthermore, tools that offer mobile apps or web-based dashboards enable administrators to manage IoT devices on the go, ensuring that critical tasks can be performed from any location. Compatibility is also a key consideration, as IoT devices often run on diverse operating systems and hardware architectures. The best solutions support a wide range of platforms, including Linux, Windows, macOS, Android, and embedded systems.
Scalability is another hallmark of the best IoT remote SSH connection tools. As IoT networks expand, the ability to manage thousands of devices simultaneously becomes essential. Leading tools offer centralized management consoles, automated scripting capabilities, and integration with cloud platforms like AWS IoT and Microsoft Azure. These features enable administrators to streamline operations and reduce manual intervention. Additionally, tools that provide detailed logging and analytics help in monitoring performance, identifying bottlenecks, and ensuring compliance with regulatory standards. By combining security, usability, compatibility, and scalability, the best IoT remote SSH connection tools empower organizations to achieve seamless and efficient device management.
How Can You Ensure Security in IoT Remote SSH Connections?
Security is the backbone of any IoT remote SSH connection, and ensuring it requires a multi-layered approach. The first step is to use strong authentication mechanisms. Passwords alone are no longer sufficient, as they are vulnerable to brute-force attacks. Instead, the best IoT remote SSH connection tools rely on public-key cryptography, where users authenticate using private keys stored securely on their devices. This method not only enhances security but also simplifies the login process by eliminating the need to remember complex passwords. Multi-factor authentication (MFA) adds an extra layer of protection by requiring users to verify their identity through a second factor, such as a one-time code sent to their mobile device.
Encryption is another critical component of securing IoT remote SSH connections. The SSH protocol uses robust encryption algorithms to protect data in transit, but administrators must ensure that outdated or weak ciphers are disabled. Regularly updating SSH software and firmware is essential to patch vulnerabilities and protect against emerging threats. Additionally, the best IoT remote SSH connection tools offer features like intrusion detection systems (IDS) and real-time monitoring, which can alert administrators to suspicious activities or unauthorized access attempts. These tools often include automated response mechanisms that can block malicious IPs or terminate suspicious sessions.
Finally, implementing network segmentation and access controls is crucial for minimizing the attack surface. IoT devices should be isolated from other parts of the network to prevent lateral movement in case of a breach. Role-based access control (RBAC) ensures that users only have access to the devices and commands necessary for their roles. Regular audits and compliance checks can help identify and rectify security gaps. By combining strong authentication, robust encryption, proactive monitoring, and access controls, organizations can ensure that their IoT remote SSH connections remain secure and resilient.
Read also:Is Zoe Mclellan Alive Everything You Need To Know About Her Life And Career
Why Is Cross-Platform Compatibility Crucucial for IoT SSH Tools?
IoT ecosystems are inherently diverse, often comprising devices that run on different operating systems, hardware architectures, and communication protocols. This diversity makes cross-platform compatibility a critical feature of the best IoT remote SSH connection tools. Without this capability, administrators face significant challenges in managing devices uniformly, leading to inefficiencies and potential security risks. For instance, a tool that works seamlessly on Linux-based IoT devices but fails to support Windows or embedded systems creates silos, complicating the management process and increasing operational overhead.
Cross-platform compatibility ensures that administrators can use a single tool to manage all their IoT devices, regardless of the underlying platform. This not only simplifies workflows but also enhances productivity by eliminating the need to switch between multiple tools. The best IoT remote SSH connection solutions support a wide range of platforms, including popular operating systems like Linux, Windows, and macOS, as well as mobile platforms like Android and iOS. Additionally, these tools are designed to work with various hardware architectures, such as ARM, x86, and MIPS, which are commonly used in IoT devices. This versatility allows administrators to maintain a consistent and streamlined approach to device management.
Moreover, cross-platform tools often come with features like automated scripting and centralized dashboards, which further enhance their utility. Automated scripts can be used to execute commands across multiple devices simultaneously, reducing manual effort and minimizing the risk of errors. Centralized dashboards provide a unified view of all connected devices, enabling administrators to monitor performance, track usage, and troubleshoot issues from a single interface. By prioritizing cross-platform compatibility, the best IoT remote SSH connection tools empower organizations to manage their IoT networks efficiently, securely, and at scale.
What Are the Top Tools for IoT Remote SSH Connections?
Selecting the right tool for IoT remote SSH connections can significantly impact the efficiency and security of your operations. Below, we explore two of the top tools that stand out in the market for their robust features and ease of use.
Tool 1: Secure Shell App for Android and iOS
The Secure Shell App is a popular choice for managing IoT devices remotely from mobile devices. Designed specifically for Android and iOS, this app provides a lightweight yet powerful solution for administrators who need to access their IoT networks on the go. One of its standout features is its intuitive interface, which allows users to establish SSH connections with just a few taps. The app supports key-based authentication, ensuring secure access without the need for passwords.
Additionally, the Secure Shell App offers advanced features like port forwarding and X11 forwarding, which are particularly useful for IoT applications that require graphical interfaces or remote debugging. The app also supports multiple simultaneous connections, enabling administrators to manage several devices at once. Its compatibility with a wide range of IoT platforms makes it a versatile tool for diverse environments. For users who prioritize mobility and convenience, the Secure Shell App is an excellent choice for IoT remote SSH connections.
Tool 2: Bitvise SSH Client for Windows
Bitvise SSH Client is a feature-rich tool designed for Windows users, offering a comprehensive suite of capabilities for managing IoT devices securely. Known for its robust security features, Bitvise supports advanced encryption algorithms and multi-factor authentication, ensuring that your IoT connections remain protected against unauthorized access. The client also includes a built-in SFTP server, enabling seamless file transfers between IoT devices and the administrator's workstation.
One of the key advantages of Bitvise SSH Client is its scripting capabilities. Administrators can automate routine tasks, such as device configuration and performance monitoring, using customizable scripts. This feature is particularly beneficial for large-scale IoT deployments, where manual intervention can be time-consuming and error-prone. Additionally, Bitvise offers a user-friendly graphical interface, making it accessible to users with varying levels of technical expertise. Its compatibility with Windows and integration with other enterprise tools make it a top choice for organizations seeking a reliable and efficient IoT remote SSH connection solution.
How to Optimize SSH Performance for IoT Devices?
Optimizing SSH performance is crucial for ensuring efficient and reliable IoT device management. One of the first steps is to configure SSH settings to minimize latency and maximize throughput. For example, disabling unnecessary encryption algorithms and compression can reduce the computational overhead on resource-constrained IoT devices. Additionally, enabling connection multiplexing allows multiple SSH sessions to share a single TCP connection, reducing the time required to establish new connections and improving overall performance.
Another effective strategy is to leverage SSH keep-alive packets, which prevent idle connections from being terminated by firewalls or network devices. By configuring keep-alive intervals, administrators can ensure that SSH sessions remain active even during periods of inactivity. This is particularly important for IoT devices that may operate in environments with intermittent connectivity. Furthermore, optimizing SSH key sizes can strike a balance between security and performance. While larger keys provide stronger encryption, they also require more computational resources. Using 2048-bit or 4096-bit keys is generally recommended for most IoT applications.
Finally, administrators should consider using lightweight SSH clients and servers that are specifically designed for IoT environments. These tools are optimized to run on devices with limited processing power and memory, ensuring that SSH operations do not overwhelm the system. Regularly updating SSH software and firmware is also essential to take advantage of performance improvements and security patches. By implementing these strategies, organizations can optimize SSH performance for their IoT devices, ensuring smooth and efficient remote management.
What Are the Common Challenges in IoT Remote SSH Connections?
While IoT remote SSH connections offer numerous benefits, they also come with their own set of challenges. One of the most common issues is the limited computational resources of IoT devices, which can make it difficult to run resource-intensive SSH protocols. Many IoT devices are designed to be lightweight and energy-efficient, leaving little room for additional processing overhead. This can result in slower connection speeds, increased latency, and even dropped sessions, especially when managing multiple devices simultaneously.
Another challenge is network instability, which is often encountered in IoT environments. Devices may be deployed in remote or harsh conditions, where connectivity is unreliable or intermittent. This can disrupt SSH sessions and make it difficult to perform critical tasks like configuration updates or troubleshooting
Unveiling The Mysteries Of The Chinese Animal Year 1984: Insights And Interpretations
What To Expect From Morning Joe Ratings In January 2025: Trends, Analysis, And Predictions
How To Use Raspberry Pi Resource Monitor SSH For Enhanced System Management
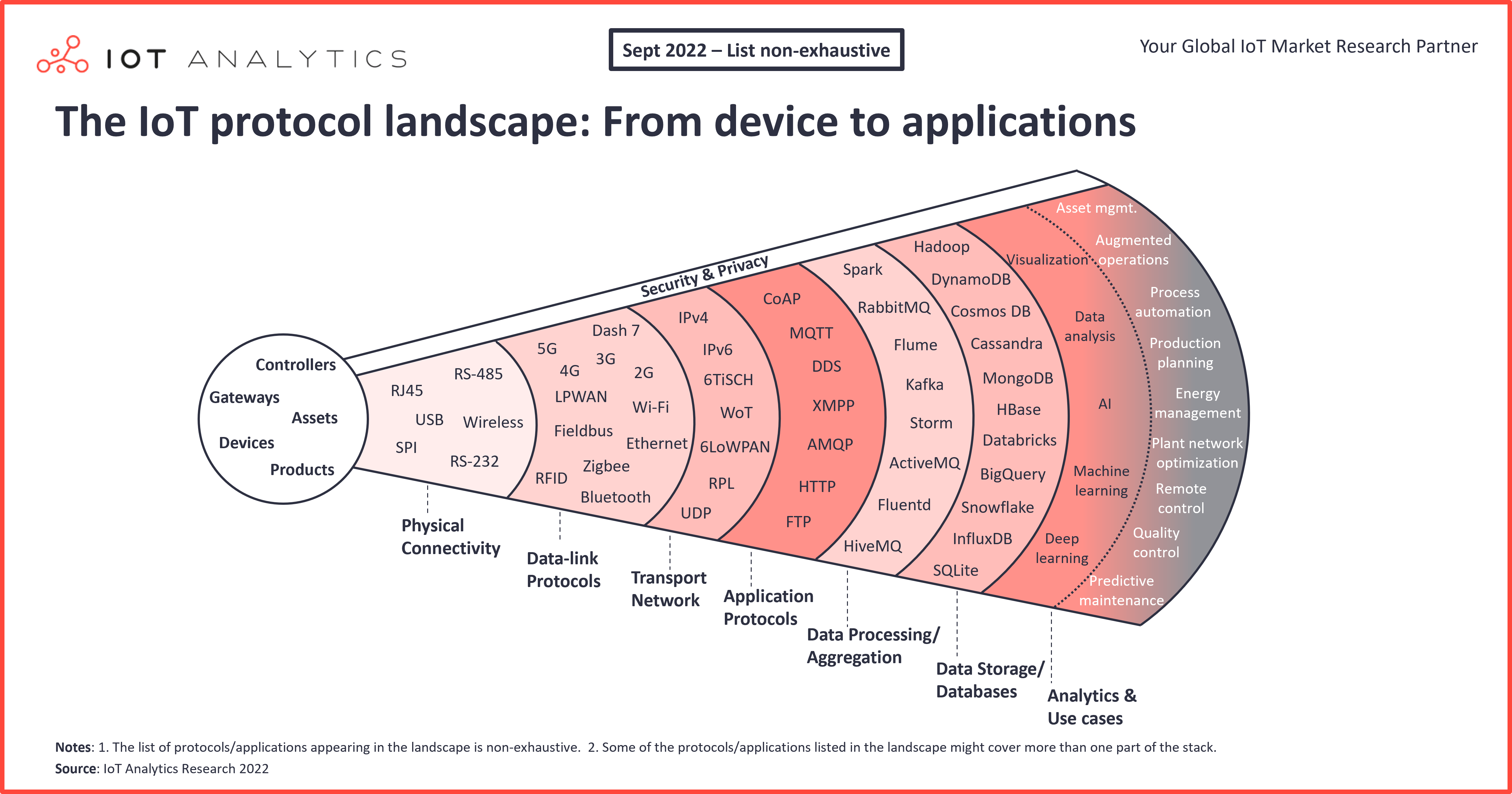
5 things to know about IoT protocols

Extended IoT Remote 7 Steps Instructables