Best IoT Remote SSH Setup: A Comprehensive Guide To Secure And Efficient Connectivity
In today's interconnected world, the ability to remotely manage IoT devices is more crucial than ever. Whether you're a developer, a system administrator, or a tech enthusiast, having the best IoT remote SSH setup can save you time, enhance security, and streamline operations. Secure Shell (SSH) is a powerful protocol that allows you to access and control devices over a network securely. By leveraging SSH, you can ensure that your IoT devices remain accessible while minimizing the risks associated with unauthorized access.
IoT devices are increasingly being deployed in a variety of environments, from smart homes to industrial automation systems. However, managing these devices remotely presents unique challenges. A robust SSH setup not only facilitates secure communication but also enables you to troubleshoot and configure devices without being physically present. With the right tools and configurations, you can achieve a seamless remote management experience that aligns with your specific needs.
As the demand for IoT solutions grows, so does the need for reliable remote access methods. In this article, we will explore the best practices for setting up SSH on IoT devices, ensuring both security and efficiency. From choosing the right hardware to configuring advanced security features, we’ll guide you through every step of the process. By the end, you’ll have a clear understanding of how to implement the best IoT remote SSH setup for your projects.
Read also:Giant Gonzales The Towering Legend Of Wwe
Table of Contents
- What is SSH and Why is it Essential for IoT?
- How to Choose the Right Hardware for IoT SSH Setup?
- Step-by-Step Guide to Configuring SSH on IoT Devices
- Best Practices for Securing Your SSH Connection
- How to Troubleshoot Common SSH Issues on IoT Devices?
- What are the Advanced Features of SSH for IoT?
- Why is Remote Access via SSH Better Than Other Methods?
- Frequently Asked Questions About IoT Remote SSH Setup
What is SSH and Why is it Essential for IoT?
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between two devices over an unsecured network. It is widely used for remote administration, file transfers, and executing commands on remote systems. For IoT devices, SSH is particularly valuable because it provides a secure way to access and manage devices without exposing them to potential threats.
IoT devices often operate in environments where physical access is limited or impractical. SSH bridges this gap by enabling administrators to perform tasks such as software updates, configuration changes, and diagnostics remotely. Moreover, SSH encrypts all data transmitted between the client and server, ensuring that sensitive information remains protected from eavesdropping or tampering.
Another reason SSH is indispensable for IoT is its versatility. It supports various authentication methods, including password-based and key-based authentication, giving users flexibility in securing their devices. Additionally, SSH can be used to tunnel other protocols, making it a powerful tool for creating secure connections in complex IoT ecosystems.
How to Choose the Right Hardware for IoT SSH Setup?
When setting up SSH for IoT devices, selecting the right hardware is a critical first step. The hardware you choose will determine the performance, security, and scalability of your IoT deployment. Here are some factors to consider:
- Processor and Memory: IoT devices often have limited computational resources. Ensure that your device has a processor and memory capable of handling SSH operations without significant latency.
- Operating System Compatibility: Verify that the device’s operating system supports SSH. Popular choices like Linux and Windows IoT Core typically include built-in SSH capabilities.
- Network Connectivity: Reliable network connectivity is essential for SSH. Devices should support Ethernet, Wi-Fi, or cellular connectivity, depending on your use case.
- Security Features: Look for hardware with built-in security features such as hardware encryption modules or Trusted Platform Modules (TPMs).
Some popular IoT hardware options include Raspberry Pi, Arduino, and industrial-grade devices like Siemens SIMATIC IoT gateways. Each of these platforms has its strengths and is suited to different applications. For example, Raspberry Pi is ideal for prototyping and small-scale deployments, while industrial gateways are better suited for mission-critical applications.
Step-by-Step Guide to Configuring SSH on IoT Devices
Installing SSH on Your IoT Device
Once you’ve selected the appropriate hardware, the next step is to install SSH on your IoT device. The process varies depending on the operating system, but here’s a general guide:
Read also:Song Kang Family A Deep Dive Into The Life And Background Of The Rising Kdrama Star
- Update the System: Before installing SSH, ensure your device’s operating system is up to date. Run the appropriate update command for your OS (e.g.,
sudo apt update && sudo apt upgradefor Linux). - Install the SSH Server: Use the package manager to install the SSH server. For example, on Linux, you can use
sudo apt install openssh-server. - Start and Enable the SSH Service: After installation, start the SSH service and configure it to run on boot. On Linux, you can use
sudo systemctl start sshandsudo systemctl enable ssh.
Configuring SSH for Secure Access
With SSH installed, the next step is to configure it for secure access. Follow these steps to enhance security:
- Change the Default Port: By default, SSH listens on port 22. Changing this to a non-standard port can reduce the risk of automated attacks.
- Disable Password Authentication: Passwords can be vulnerable to brute-force attacks. Instead, use key-based authentication for added security.
- Set Up a Firewall: Use a firewall to restrict access to the SSH port, allowing only trusted IP addresses.
By following these steps, you can ensure that your SSH setup is both functional and secure, providing a solid foundation for remote management of your IoT devices.
Best Practices for Securing Your SSH Connection
Securing your SSH connection is paramount to protecting your IoT devices from unauthorized access. Here are some best practices to consider:
- Use Strong Passwords or SSH Keys: If you must use passwords, ensure they are complex and unique. However, SSH keys are a more secure alternative.
- Implement Two-Factor Authentication (2FA): Adding an extra layer of security can significantly reduce the risk of unauthorized access.
- Regularly Update SSH Software: Keep your SSH server software up to date to patch any vulnerabilities.
- Monitor SSH Logs: Regularly review SSH logs to detect and respond to suspicious activity.
By adhering to these best practices, you can minimize the risk of security breaches and ensure that your IoT devices remain safe and accessible.
How to Troubleshoot Common SSH Issues on IoT Devices?
Even with the best IoT remote SSH setup, you may encounter issues that require troubleshooting. Here are some common problems and their solutions:
- Connection Refused: This error typically occurs when the SSH service is not running or the port is blocked. Check the SSH service status and your firewall settings.
- Authentication Failed: Ensure that your credentials are correct and that key-based authentication is properly configured.
- Slow Connection: High latency can be caused by network issues or resource constraints on the IoT device. Optimize your network and device performance to address this.
By systematically addressing these issues, you can maintain a reliable and efficient SSH connection for your IoT devices.
What are the Advanced Features of SSH for IoT?
SSH offers several advanced features that can enhance the functionality of your IoT remote SSH setup:
- Port Forwarding: Use SSH to forward ports securely, enabling access to services running on your IoT device.
- SSH Tunnels: Create encrypted tunnels to securely transfer data between devices.
- Automated Tasks: Use SSH scripts to automate routine tasks such as backups and updates.
These features can significantly improve the efficiency and flexibility of your IoT deployments.
Why is Remote Access via SSH Better Than Other Methods?
While there are various methods for remote access, SSH stands out for several reasons:
- Security: SSH encrypts all data, ensuring that sensitive information is protected.
- Versatility: SSH supports multiple authentication methods and can be used for a wide range of tasks.
- Performance: SSH is lightweight and efficient, making it ideal for resource-constrained IoT devices.
By leveraging SSH, you can achieve a secure and efficient remote access solution that meets the demands of modern IoT environments.
Frequently Asked Questions About IoT Remote SSH Setup
What Are the Key Benefits of Using SSH for IoT Devices?
SSH provides secure, encrypted communication, enabling safe remote access to IoT devices. It also supports automation and advanced features like port forwarding.
How Can I Improve the Security of My SSH Setup?
Use strong authentication methods, change the default port, and regularly update your SSH software to enhance security.
Can SSH Be Used for Large-Scale IoT Deployments?
Yes, SSH is scalable and can be used effectively in large-scale IoT deployments with proper configuration and management.
In conclusion, the best IoT remote SSH setup is a cornerstone of modern IoT management. By following the guidelines and best practices outlined in this article, you can ensure secure, efficient, and reliable remote access to your IoT devices. Whether you’re managing a single device or an entire network, SSH provides the tools you need to succeed.
For more information on securing IoT devices, visit Cloudflare's Guide to SSH.
How To Download Remote IoT VPC For Free: A Comprehensive Guide
How To Successfully Plan And Execute A Project: A Comprehensive Guide
Mastering The Management Of Raspberry Pi Remotely With RemoteIoT Management Platform
5 things to know about IoT protocols
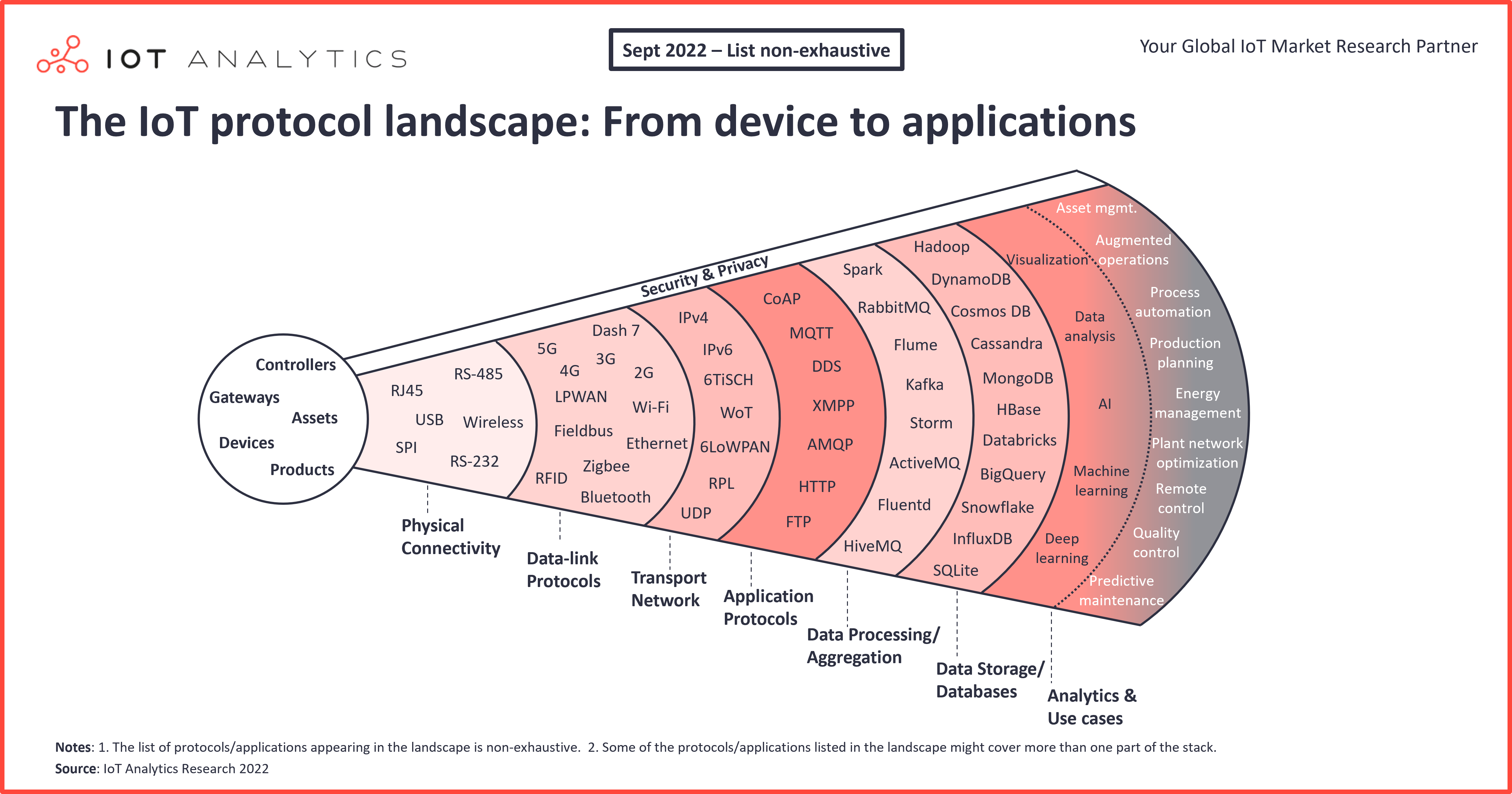
5 things to know about IoT protocols