Securely Connect RemoteIoT VPC: A Comprehensive Guide For Enhanced Security And Performance
In today's interconnected world, securely connecting to a RemoteIoT Virtual Private Cloud (VPC) is essential for businesses and individuals alike. With the increasing reliance on cloud-based infrastructure, ensuring secure and reliable access to your VPC is crucial for maintaining data integrity, protecting sensitive information, and optimizing performance. Whether you're managing IoT devices, running applications, or handling critical data, understanding how to securely connect to your RemoteIoT VPC can significantly impact your operations.
As cyber threats continue to evolve, implementing robust security measures becomes paramount. The RemoteIoT platform offers advanced features that enable secure VPC connections, but knowing how to leverage these tools effectively requires a comprehensive understanding of the underlying technologies and best practices. This article will guide you through the essential steps and considerations for establishing a secure connection to your RemoteIoT VPC, while also exploring various security protocols and optimization techniques.
Throughout this guide, we'll delve into the technical aspects of VPC connections, discuss different authentication methods, and provide practical implementation strategies. We'll also examine real-world applications and case studies that demonstrate the importance of secure VPC connections in various industries. By following these guidelines and best practices, you can ensure that your RemoteIoT VPC remains protected while maintaining optimal performance for your applications and devices.
Read also:Actor Kurt Russell
Table of Contents
- Understanding RemoteIoT VPC Architecture
- Essential Security Protocols for VPC Connections
- Advanced Authentication Methods
- Network Optimization Techniques
- Step-by-Step Implementation Guide
- Monitoring and Maintenance Tools
- Real-World Case Studies
- Compliance and Regulatory Standards
- Troubleshooting Common Issues
- Future Trends in VPC Security
Understanding RemoteIoT VPC Architecture
The RemoteIoT VPC architecture is designed to provide a secure and isolated environment for running applications and managing IoT devices. At its core, the VPC operates as a logically isolated section of the cloud, allowing users to launch resources in a virtual network that they define. This architecture includes several key components:
- Subnets for organizing resources
- Routing tables for traffic management
- Network access control lists (ACLs)
- Security groups for instance-level protection
Core Components of RemoteIoT VPC
The VPC's architecture is built upon multiple layers of security and networking features. These include:
- Virtual Private Network (VPN) gateways
- Internet gateways for external communication
- Network address translation (NAT) instances
- Elastic IP addresses for resource identification
Benefits of VPC Isolation
The isolation provided by RemoteIoT VPC offers several advantages:
- Enhanced security through network segmentation
- Improved performance with dedicated resources
- Better control over network configuration
- Customizable IP address ranges
Essential Security Protocols for VPC Connections
When connecting to your RemoteIoT VPC, implementing the right security protocols is crucial for maintaining a secure environment. Several industry-standard protocols can be utilized to ensure secure communications:
- Transport Layer Security (TLS) for encrypted data transfer
- Secure Shell (SSH) for remote access
- Internet Protocol Security (IPsec) for network-level protection
- Virtual Private Network (VPN) protocols
Implementing TLS in VPC Connections
Transport Layer Security (TLS) plays a vital role in securing VPC connections by encrypting data in transit. To implement TLS effectively:
- Use certificates from trusted Certificate Authorities (CAs)
- Implement mutual TLS authentication
- Regularly update TLS versions and cipher suites
- Monitor certificate expiration dates
IPsec Configuration Best Practices
Internet Protocol Security (IPsec) provides robust network-level protection for VPC connections. Key best practices include:
Read also:Stacy Cruz A Rising Star In The Entertainment Industry
- Implementing strong encryption algorithms
- Using pre-shared keys or digital certificates
- Configuring proper security associations
- Regularly reviewing and updating IPsec policies
Advanced Authentication Methods
Secure authentication is a critical component of connecting to your RemoteIoT VPC. Modern authentication methods offer enhanced security while maintaining usability:
- Multi-Factor Authentication (MFA)
- OAuth 2.0 and OpenID Connect
- Public Key Infrastructure (PKI)
- Single Sign-On (SSO) solutions
Implementing Multi-Factor Authentication
Multi-Factor Authentication (MFA) adds an extra layer of security to VPC connections. To implement MFA effectively:
- Require both something the user knows and something they have
- Use time-based one-time passwords (TOTP)
- Integrate hardware security keys
- Implement adaptive authentication policies
PKI Implementation Guidelines
Public Key Infrastructure (PKI) provides a robust framework for secure authentication. Key implementation guidelines include:
- Establishing a certificate authority hierarchy
- Implementing certificate revocation mechanisms
- Using strong key lengths and algorithms
- Regularly auditing certificate usage
Network Optimization Techniques
Optimizing your VPC network performance is essential for maintaining efficient operations. Several techniques can be employed to enhance network performance while maintaining security:
- Implementing proper subnet design
- Optimizing routing tables
- Using elastic load balancers
- Implementing content delivery networks (CDNs)
Subnet Design Best Practices
Effective subnet design can significantly impact VPC performance. Key best practices include:
- Segmenting subnets by function or security level
- Using appropriate CIDR blocks
- Implementing network address translation (NAT)
- Configuring proper network ACLs
Load Balancing Strategies
Implementing load balancing can improve both performance and reliability. Key strategies include:
- Using application load balancers
- Implementing cross-zone load balancing
- Configuring health checks
- Implementing SSL termination
Step-by-Step Implementation Guide
Establishing a secure connection to your RemoteIoT VPC requires careful planning and execution. Follow these steps to ensure a successful implementation:
- Plan your VPC architecture and security requirements
- Set up necessary network components
- Configure security groups and network ACLs
- Implement authentication mechanisms
- Test and validate connections
- Monitor and maintain security configurations
Initial Setup Considerations
Before beginning implementation, consider the following:
- Define clear security policies
- Identify required network resources
- Plan for scalability and future growth
- Establish monitoring and alerting mechanisms
Testing and Validation Procedures
After implementation, thorough testing is crucial:
- Conduct penetration testing
- Verify authentication mechanisms
- Test failover scenarios
- Validate performance metrics
Monitoring and Maintenance Tools
Continuous monitoring and maintenance are essential for maintaining secure VPC connections. Several tools and techniques can help:
- CloudWatch for performance monitoring
- CloudTrail for activity logging
- Security Hub for threat detection
- Third-party monitoring solutions
Implementing Monitoring Solutions
Effective monitoring requires proper configuration:
- Set up custom metrics and alarms
- Configure log retention policies
- Implement real-time alerting
- Regularly review monitoring data
Maintenance Best Practices
Regular maintenance helps ensure ongoing security:
- Apply security patches promptly
- Rotate authentication credentials
- Review and update security policies
- Conduct regular security audits
Real-World Case Studies
Examining real-world applications can provide valuable insights into secure VPC connections:
- Case study: Healthcare organization implementing secure VPC for patient data
- Case study: Financial institution using VPC for secure transactions
- Case study: Manufacturing company connecting IoT devices through VPC
Healthcare Sector Implementation
A healthcare provider successfully implemented secure VPC connections by:
- Using HIPAA-compliant security measures
- Implementing strict access controls
- Utilizing encryption for all data transfers
- Conducting regular security audits
Financial Institution Case Study
A major bank enhanced its security by:
- Implementing multi-layered authentication
- Using advanced threat detection systems
- Conducting regular penetration testing
- Maintaining strict compliance standards
Compliance and Regulatory Standards
Meeting compliance requirements is crucial for many organizations using VPC connections:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- ISO 27001 Information Security Management
GDPR Compliance Considerations
To comply with GDPR requirements:
- Implement data encryption mechanisms
- Establish data protection policies
- Conduct regular privacy impact assessments
- Maintain proper documentation
HIPAA Compliance Guidelines
For healthcare organizations:
- Implement business associate agreements
- Use secure data transfer protocols
- Maintain audit trails
- Conduct regular risk assessments
Troubleshooting Common Issues
When connecting to your RemoteIoT VPC, several common issues may arise:
- Connectivity problems
- Authentication failures
- Performance bottlenecks
- Security configuration errors
Connectivity Troubleshooting Steps
To resolve connectivity issues:
- Verify network configurations
- Check security group rules
- Test routing tables
- Examine network ACLs
Performance Optimization Techniques
For performance issues:
- Optimize instance types
- Implement caching mechanisms
- Use content delivery networks
- Optimize database
Retro Bowl: A Nostalgic Journey Into Classic Football Gaming
Discover The Magic Of Jackerman 3D: A Comprehensive Guide To 3D Printing Innovation
Mothers Warmth 3 Jackerman: A Comprehensive Guide To Embracing Family Bonds

Centralized VPC Endpoints what they are and how to connect securely
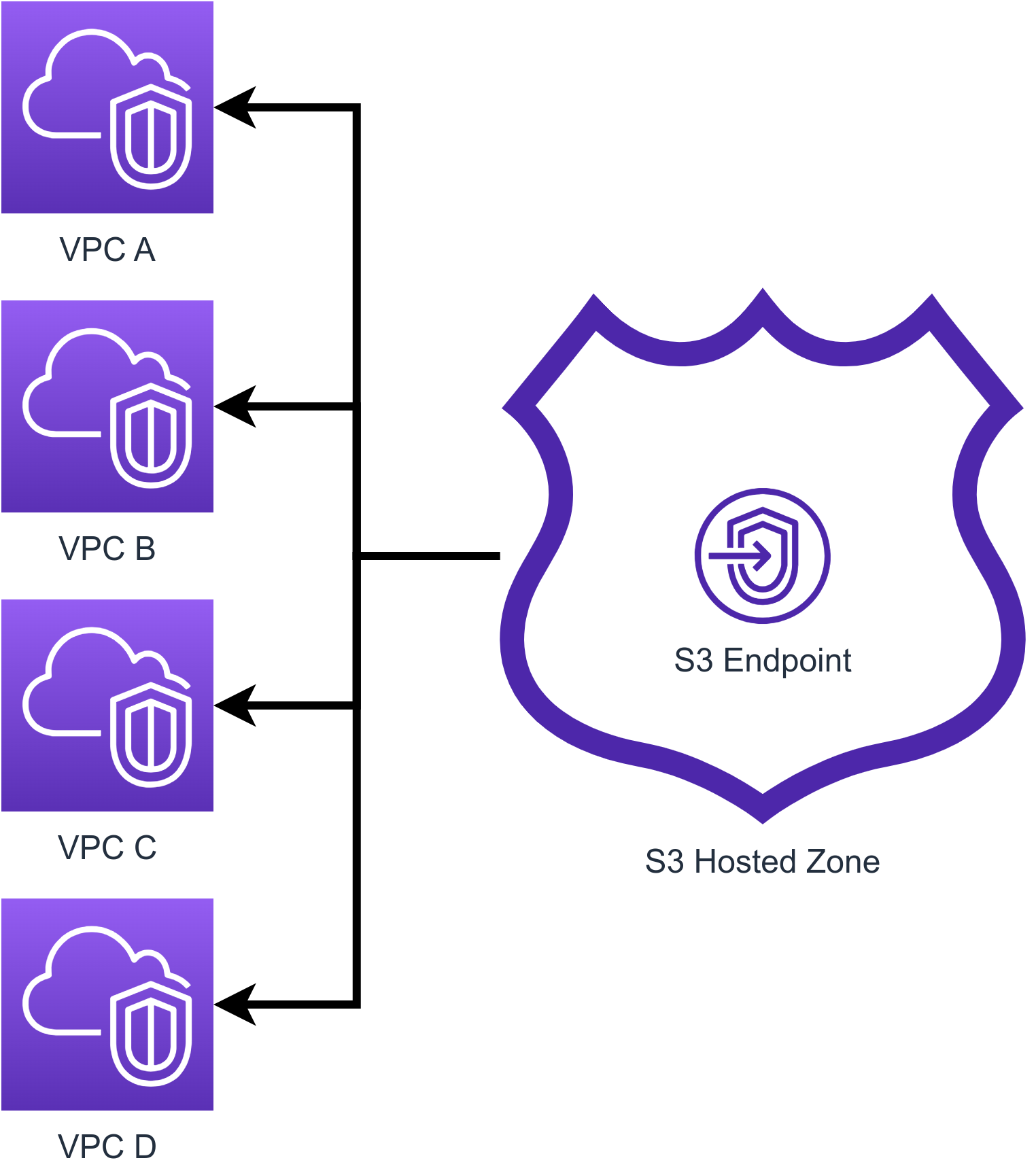
Centralized VPC Endpoints what they are and how to connect securely